Information Security
MAS utilizes partnerships and products to deliver services that protect all Windows-based systems against malware. Understanding that your information is critical to your business, we employ leading edge technology and solutions to protect your information as well as your IT systems. We focus on detecting threats and eliminating them. Our solution:
- Protects the confidentiality of data
- Preserves the integrity of data
- Ensures the availability of data for authorized use
Cloud Migration Services
- Email that never goes down for maintenance
- File Sharing
- Shared Calendaring
- Access to data from wherever, whenever or from any device with an internet connection
- Word, Excel, PowerPoint, Outlook, OneNote, Publisher
- Online meetings, Web Conferencing, Instant messaging
Technology Consulting
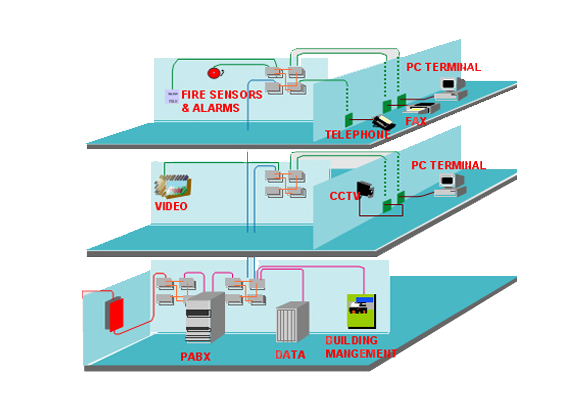
Communication; VOIP, Cabling and Security
Computer repair
As noted above there are many points of failure when it comes to computers. In fact the scenarios listed do not take in to account the human element. We could add dropped computers, water or other liquid spills to the list. The point is that inevitably even the best computers fail. Our engineers have the skills and experience necessary to handle any type of repair. They have the knowledge, cutting-edge industry tools, and training necessary to make sure your computer gets back up with minimal impact to your operations or work product.

Network Monitoring and Management
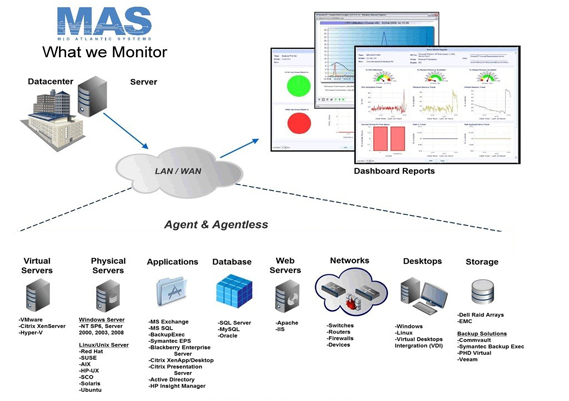
Data Management
- Manage backups and growing data requirements efficiently which will result in the delivery of enhanced RTOs (recovery time objectives) and RPOs (Recovery point objectives). The actual objectives will be negotiated up front and included in the project management plan as an SLA (service level agreement).
- Centralized, unified point where the information is stored. Assured recovery is one of our unique features that guarantees all of your data bases will be corruption free.
Dual protection is the practice of boosting your local backup plan by adding an additional redundant offsite plan. By storing your backups both locally and offsite, you effectively double your protection and guarantee reliable access to your data in the event of a disaster. By leveraging both local and offsite storage, you get the best of both worlds:

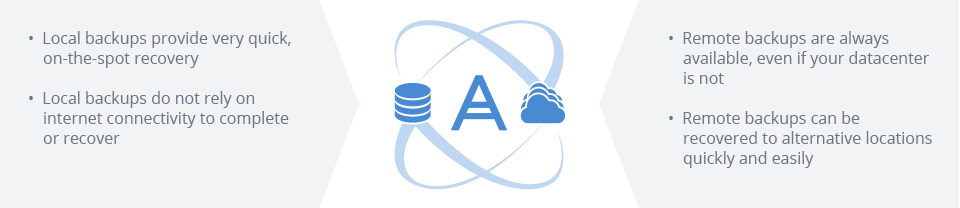
Although there are several ways to design a dual protection strategy, the 3-2-1 rule produces the most effective, reliable results:
